SpamShield can be used solely for User's own personal or internal business purposes. The User may not commercially distribute, sublicense, resell, or otherwise transfer for any consideration, or reproduce for any such purposes, the SpamShield software or any modification or derivation thereof, either alone or in conjunction with any other product or program. Further, the User may not modify the SpamShield Software, other than for User's own personal or internal business use.
THIS SPAMSHIELD SOFTWARE IS PROVIDED TO THE USER "AS IS." THE AUTHOR MAKES NO WARRANTIES, EITHER EXPRESS OR IMPLIED, WITH RESPECT TO THIS SPAMSHIELD SOFTWARE AND/OR ASSOCIATED MATERIALS PROVIDED TO THE USER, INCLUDING BUT NOT LIMITED TO ANY WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR AGAINST INFRINGEMENT. THE AUTHOR OF SPAMSHIELD SOFTWARE DOES NOT WARRANT THAT THE FUNCTIONS CONTAINED IN THE SOFTWARE WILL MEET YOUR REQUIREMENTS, OR THAT THE OPERATION OF THE SOFTWARE WILL BE UNINTERRUPTED OR ERROR-FREE, OR THAT DEFECTS IN THE SOFTWARE WILL BE CORRECTED. FURTHERMORE, NO WARRANTIES OR ANY REPRESENTATIONS ARE MADE REGARDING THE USE OR THE RESULTS OF THE USE OF THE SOFTWARE OR ANY DOCUMENTATION PROVIDED HEREWITH IN TERMS OF THEIR CORRECTNESS, ACCURACY, RELIABILITY, OR OTHERWISE. NO ORAL OR WRITTEN INFORMATION OR ADVICE GIVEN BY THE AUTHOR OF SPAMSHIELD SOFTWARE SHALL CREATE A WARRANTY OR IN ANY WAY INCREASE THE SCOPE OF THIS WARRANTY.
LIMITATION OF LIABILITY -- THE AUTHOR OF SPAMSHIELD SOFTWARE AND ITS LICENSORS ARE NOT LIABLE FOR ANY CLAIMS OR DAMAGES WHATSOEVER, INCLUDING PROPERTY DAMAGE, PERSONAL INJURY, INTELLECTUAL PROPERTY INFRINGEMENT, LOSS OF PROFITS, OR INTERRUPTION OF BUSINESS, OR FOR ANY SPECIAL, CONSEQUENTIAL OR INCIDENTAL DAMAGES, HOWEVER CAUSED, WHETHER ARISING OUT OF BREACH OF WARRANTY, CONTRACT, TORT (INCLUDING NEGLIGENCE), STRICT LIABILITY, OR OTHERWISE.
Spam refers to the flooding of Internet with many copies of the same message, in an attempt to force the message on people who would not otherwise choose to receive it. Most spam is commercial advertising, often for dubious products, get-rich-quick schemes, or quasi-legal services (see http://spam.abuse.net for more information).
If you are an active Internet user, you have a good chance of being spotted by a spammer. You can take a few basic precautions to avoid being spammed.
A typical email header looks like,
Received: from relay1.mailsrvcs.net ([192.168.129.40]) by mta1.gte.net (Intermail v3.1 117 234) with ESMTP id
<19980209012141.GIAZ23622@relay1.mailsrvcs.net> for <xxx@xxx.com>; Sun, 8 Feb 1998 19:21:41 -0600
Received: from quantex (port31.blmh.prodigy.net [204.237.36.31]) by mail1y-int.prodigy.net (8.8.5/8.8.5) with ESMTP id UAA27350
for <xxx@xxx.com>; Sun, 8 Feb 1998 20:16:36 -0500
Message-Id: <199802090116.UAA27350@mail1y-int.prodigy.net>
From: "Somebody" <somebody@somedomain.com>
To: <xxx@xxx.com>
Subject: Hi
Date: Sun, 8 Feb 1998 20:04:52 -0500
MIME-Version: 1.0
Content-Type: text/plain; charset=ISO-8859-1
Spammers hide their identity by faking some of the email headers. Except for a few Received: fields, all the other fields can be changed to anything the sender wishes to. Although spammers fake their identity in many ingenious ways, we can spot some patterns
The problem with many anti spamming tools, which work with a database of spammers, is that the database needs constant updates as the spammers change their identity too often. SpamShield provides a powerful, programmatic access to all the header fields in the email. You could create a rule which trashes all the mails that have the same From and To fields or a Received field having a specific domain name.
Download SpamShield.zip and extract the contents into an existing directory. SpamShield package ships with the following files.
SpamShield.exe : SpamShield executable
SpamShield.cfg : SpamShield configuration file
SpamShield.dat : SpamShield data file
Readme.txt : Pre installation information
License.txt : License information
SpamShield.htm : Help file in HTML format
General.jpg : Part of the help system
Bounce.jpg : Part of the help system
Server.jpg : Part of the help system
Rule.jpg : Part of the help system
User.jpg : Part of the help system
SpamShield.cfg and SpamShield.dat are configuration and data files for SpamShield. Take a moment to look into them; they are plain ascii files. Be warned that they will be overwritten very often when SpamShield is running. SpamShield depends on Windows Sockets, which is a standard DLL in Windows 95.
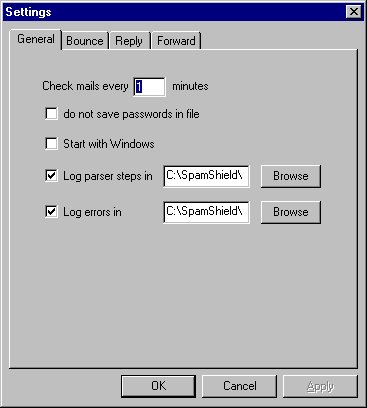
When you start SpamShield, a small icon appears on the system tray (on the right corner of your system task bar). Click the right button and choose Properties menu item. The Properties dialog pops up

In the General settings,
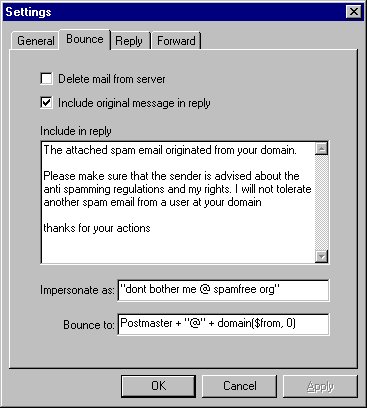
Bounce setting will be used when a Bounce action is associated with a Rule
Not implemented in this version
Not implemented in this version
Click the right button on the SpamShield icon on the system tray and choose Mail Accounts menu item. The Mail Accounts dialog pops up. You can add any number of users, rules and servers.
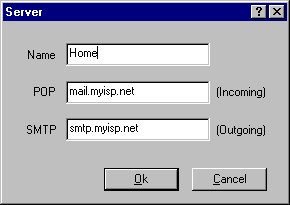
Click on the server tab. Click on Add button. Enter a name for the server (this name is for display & storing purposes only). POP (Post Office Protocol) server is the host machine that stores a mailbox and the emails received for that address. Enter the POP server's domain name (e.g., pop.johndoe.com). SMTP (Simple Mail Transfer Protocol) server is the host machine that sends out an email. Enter SMTP server's domain name (e.g., smtp.johndoe.com). You can also enter their IP addresses instead of their domain names (e.g., 123.45.54.23)
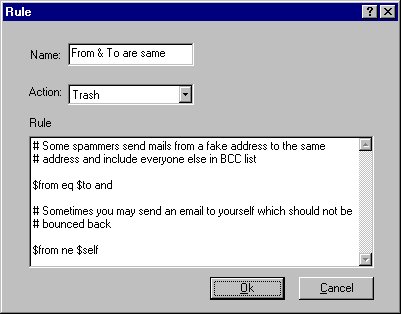
Click on the Rule tab and click on the Add button. The Rule dialog pops up. Enter a name for the rule and select an action to be performed when the rule evaluates to true. Currently Trash and Bounce are the only two actions supported. In the Rule edit control, construct a rule that would evaluate to true or false. Refer to the Grammar section for programming constructs. When you close the dialog by pressing Ok, the Rule will be parsed for syntax errors. The words in the rule will be highlighted till the invalid word is encountered. You cannot dismiss this dialog with a syntax error in the Rule.
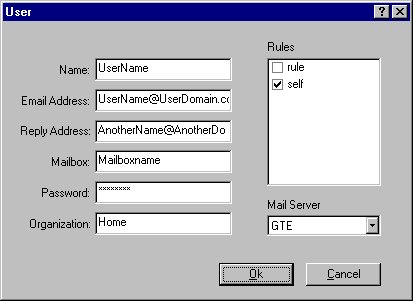
Click on the User tab and click on the Add button. Enter a display name for the user. Enter a valid Email Address and Reply Address. This email address will be used to connect to your POP server. Reply address is used in the bounced mails when you leave the Impersonator name (in Bounce setting) empty. You must select a server in the Mail Server combo box to activate the MailBox and Password controls. Organization name will be used in the bounced mail header. All the rules are listed in the Rules list box. Only the checked rules will be evaluated while checking this user's mailbox. If you leave the Password empty, you will be prompted for the password when SpamShield starts up.
In SpamShield, users have one or more rules associated with them that will be applied to every email received in the user's mailbox. The rules are evaluated in the context of the received mail and if they evaluate to true, the action associated with that rule is executed. Currently Trash and Bounce are the only two actions supported. A rule is a logical expression constructed from the predefined system variables, operators and built-in functions described in the next section.
A rule is a logical expression; an expression that evaluates to true or false. A logical expression can be one or more sub expressions bound together by AND, OR or NOT. The sub expressions can be formed of relational expressions EQ and NE (equal and not equal) or from a built-in function. The grammar is not case sensitive; i.e., $From is same as $FROM which is same as $from. The equal and not equal operators compare the operands in a case-insensitive way. For example, if the mail header has From: someone@somedomain.com, the rule "$From eq "SOMEONE@SomeDomain.COM" will evaluate to true.
A comment in a rule is a # (pound sign) followed by anything until end of line. The grammar tokens can be separated by any number of blank spaces, tabs and empty lines.
The following words have special meaning within SpamShield grammar and cannot be used as an email address or domain name. Some of these keywords are not used in this version of SpamShield
EQ, NE, AND, OR, NOT, IN, MAILID, DOMAIN, LOOKUP, RECEIVED (and LT, GT, LE, GE, LIKE, NULL)
A variable is a sequence of alphabets, numbers, underscore, @ or period(.). For example, bad.spammer@machine1.johndoe.com is a variable. Variables in SpamShield will usually be either email addresses or domain names. Although email addresses can have other characters (like -, /, # etc.), they would conflict with the grammar definition. To define an email address with such characters, enclose it within single or double quotes like "address/with#/special chars@ xyz-re.com"
Variable names with a $ prefix are system variables, predefined by SpamShield (e.g., $From). All the email header fields are defined as system variables and they hold the value of the corresponding field from the email header being processed. i.e., $From holds the value of From: field, $To holds the value of To: field, $Subject holds the value of Subject: field from the mail header being processed. In fact, you can use $ prefix for any variable; if such a variable is not found in the email, it will have a null value (For example, $MyField will be empty if MyField: field is not defined in the mail header). A special system variable $self is predefined to have a value of your email address.
Some of the mail header fields appear more than once (like Received) while some have more than one value (like To, Cc fields). To be able to access all the values, the system variables are actually defined as arrays; the values can be accessed using 'C' like indices (e.g., $Received[0]), the index starting at 0. The general rule of indexing is that index 0 refers to the first occurrence of the field in the mail header (top to bottom) and increases for subsequent occurrences. An invalid index will result in an empty value. There are two exceptions to this general rule
Usually all the system variables retain the exact value from the mail header. For example, in the mail header
Message-Id: <199802090116.UAA27350@mail1y-int.somedomain.net>
$Message-Id will have the value <199802090116.UAA27350@mail1y-int.somedomain.net>. In case of From:, To: and Cc: fields, the values are parsed and
altered. For example, in the mail header
To: "john" <john@johndoe.com>
$To[0] will be john@johndoe.com (without the alias and angle brackets). This eases the programming efforts.
Using a system variable without an index will have different meanings depending on the context. For example, in the expression, "$From eq $To", only the first values of the variables are used ($From[0] eq $To[0]), while in an expression like, "$From in $To", $To will have all the values To: field had in the mail header.
The operators have similar look to C or SQL operators. Most operators have multiple representations and you can use a form that is convenient to you. The following is a list of operators in ascending order of precedence
| Operator | Representation |
| Logical OR | |, ||, or |
| Logical AND | &, &&, and |
| Not equal to | !=, <>, ne |
| Equal to | =, ==, eq |
| Greater than or equal to | >=, ge |
| Less than or equal to | <=, le |
| Greater than | >, gt |
| Less than | <, lt |
| not | !, not |
| set | in |
The precedence order can be changed by enclosing the operation in parentheses
The following are the built-in functions.
LOOKUP($variable). This function evaluates to true if the variable is found in the mail header of the mail being processed for that rule. For example, Lookup($MyHeader) will result in true if MyHeader: is found in the mail header.
DOMAIN(variable, index). This function can be used to parse an email address for the tokens that form the domain. Variable should be a standard email address
and the index can be greater than or equal to zero. If index is zero, this function returns the entire domain address that follows '@' in the email address. If index is 1,
it returns the last part of the domain (like com, edu, us, in, mil etc.). If index is 2, this function returns the domain part before the last an so on. For an email address
having the From field, SomeEmailAddress@UserMachine1.Department.SubDomain.Domain.com,
DOMAIN($From, 0) returns UserMachine1.Department.SubDomain.Domain.com
DOMAIN($From, 1) returns com
DOMAIN($From, 2) returns Domain
DOMAIN($From, 3) returns SubDomain
...
For an invalid index, DOMAIN returns an empty value
MAILID(variable). This function returns the mailbox name (mailid) from the given email address. For example, MAILID(SomeOne@SomeDomain.com) returns SomeOne. You can use any system variable that has an email address syntax ($From, $To[0], $Cc[2] etc.)
RECEIVED(variable, index). This function should be used on Received: field header strings to retrieve the From and By parts. A typical Received field looks like,
Received: from sender.someDomain.com (listserv.i-have-modified.com [123.45.67.89]) by receiver.i-have-modified.com (*private*/SMI-SVR4) with ESMTP id
UAA06851 for <subscribers@somedomain.com>; Fri, 17 Apr 1998 20:20:00 -0400 (EDT)
RECEIVED($Received[0], From) returns sender.someDomain.com, and
RECEIVED($Received[0], By) returns receiver.i-have-modified.com
# This rule trashes the emails that were sent to you as a blind carbon copy
NOT $self IN $To
# This rule trashes the emails that were sent from an address to the same address and you were in BCC
# Sometimes you might send an email to yourself, which should not be trashed
$From = $To && $From != $Self
# Use this rule if you know all the domains you receive normal emails from
NOT DOMAIN($From, 0) IN ( domain1.com, "special-domain.edu", 'another/domain/dom.us' )
# This rule looks into the Received fields rather than the From or To fields
(RECEIVED($Received[0], From) = "SpammerDomain.com" || RECEIVED($Received[1], From) = "SpammerDomain.com")
All trademarks and service marks are the property of their respective owners. The domain names and email addresses used for illustration purposes are purely fictitious.